Crypto Key Generate Rsa Mod 2048
And GnuPG asks kind of key. Select RSA and RSA. Please select what kind of key you want: (1) RSA and RSA (default) (2) DSA and Elgamal (3) DSA (sign only) (4) RSA (sign only) Your selection? 1 RSA keys may be between 1024 and 4096 bits long. And select 2048-bit (as Gnuk Token only suppurt this). What keysize do you want? (2048) Requested.
- Crypto Key Generate Rsa Mod 2048 X
- Crypto Key Generate Rsa Command
- Crypto Key Generate Rsa Mod 2048 Free
KB ID 0000173
Problem
Quite a while ago I wrote the “Connecting to and managing Cisco firewalls” article, which is still pretty complete, but I’ve been asked on a few occasions, “How do I actually configure the firewall to allow remote administration via, SSH, or HTTPS/ASDM, or Telnet
If you have no network connection to the firewall, then you will need to connect via console cable (CLICK HERE).
- This document describes how I generate 2048-bit RSA keys. Here is the log to generate signature key and encryption subkey. I invoke GnuPG with -gen-key option.
- Oct 15, 2014 The ASA will retain all keys over a reboot as long as a 'write mem' is done after the keys are created. This applies to the 'RSA-Key' that is created by 'crypto key generate rsa' and the 'RSA-Key.server' key that is created upon the first ssh connection to the ASA.
Solution
Cisco ASA Allow SSH – Via Command Line
1. Log on to the firewall > Go to enable mode > Go to configure terminal mode.
2. Now you can either allow access for one machine, or a whole network, the syntax is “ssh {ip address} {subnet mask} {interface that you will be connecting to}.
3. You will need to create a username and password for SSH access, then set SSH to use the LOCAL database to check of usernames and passwords, (unless you are using LDAP, RADIUS, TACACS, or Kerberos for authentication.)
4. By default the SSH session times out after 5 mins, I prefer to change this to 45 minutes.
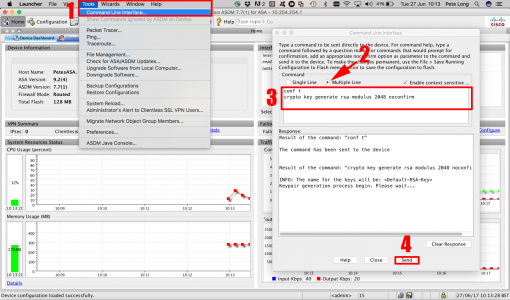
5. To encrypt the SSH access you need to have an RSA keypair on the firewall, (Note: this is generated from the firewall’s host name, and its domain name, if you ever change either, the keypair will break, and SSH access will cease until the keypair is re-created). To create a key issue a “crypto key generate rsa” command;
Note: I set the key size to 2048, this is considered good practice
7. Lastly, save the changes with a “write mem” command;
Cisco ASA Allow SSH – Via ASDM (version shown 6.4(7))
1. Connect via ASDM > Navigate to Configuration > Device Management > Management Access > ASDM/HTTPS/Telnet/SSH > Add > Select SSH > Supply the IP and subnet > OK. (Note you can set both the timeout, and the SSH versions you will accept, on this page also). Note you still need to generate the RSA Key (See step 5 above, good luck finding that in the ASDM – see the following article).
Cisco ASA – Enable AAA for SSH (Local Database) ASDM version 6.4(7)
Cisco ASA – Add a User to the Local Database
Cisco ASA – Allow HTTPS/ASDM – Via Command Line
1. Log on to the firewall > Go to enable mode > Go to configure terminal mode.
2. Now you can either allow access for one machine or a whole network, the syntax is “http {ip address} {subnet mask} {interface that it’s connected to}.
3. Unlike telnet and SSH, HTTPS/ADSM access is via the firewalls enable password (Unless you have enabled AAA logon). this password is set with the “enable password {password}” command. (Note: You will already have entered this password in step 1, only do this if you wish to change it).
4. You need to make sure that HTTPS access is enabled with a “http server enable” command.
5. Lastly, save the changes with a “write mem” command.
Cisco ASA – Allow HTTPS/ASDM – Via ASDM (version shown 6.4(7))
OK, the title of this might raise an eyebrow, but if you have access to the ASDM and you want to grant access to another IP/Network them you might want to do this. Connect via ASDM > Navigate to Configuration > Device Management > Management Access > ASDM/HTTPS/Telnet/SSH > Add > Select ASDM/HTTPS > Supply the IP and subnet > OK. (Note: You can also enable and disable the http Server here and change its port number).
Cisco ASA Allow Telnet – Via Command Line
WARNING: Telenet is insecure, if possible don’t use it, (usernames and password are sent unencrypted.)
1. Log on to the firewall > Go to enable mode > Go to configure terminal mode.
2. Now you can either allow access for one machine, or a whole network, the syntax is “telnet {ip address} {subnet mask} {interface that its connected to}.
3. To set the password you use the “passwd” command (yes that’s spelled correctly).
4. By default the telnet session times out after 5 mins, I prefer to change this to 45 minutes.
5. Lastly, save the changes with a “write mem” command.
Allow Telnet – Via ASDM (version shown 6.4(7))
1. Connect via ASDM > Navigate to Configuration > Device Management > Management Access > ASDM/HTTPS/Telnet/SSH > Add > Select Telnet > Supply the IP and subnet > OK. (Note you can set the timeout on this page also).
Related Articles, References, Credits, or External Links
Original Article Written 30/01/11
Crypto Key Generate Rsa Mod 2048 X
- October 2, 2015
- Posted by: Syed Shujaat
- Category: Cisco, Networking Solutions
Use this command to generate RSA key pairs for your Cisco device (such as a router). keys are generated in pairs–one public RSA key and one private RSA key.
If your router already has RSA keys when you issue this command, you will be warned and prompted to replace the existing keys with new keys.
NOTE: Before issuing this command, ensure that your router has a hostname and IP domain name configured (with the hostname and ipdomain-name commands).
You will be unable to complete the cryptokeygeneratersacommand without a hostname and IP domain name. (This situation is not true when you generate only a named key pair.)
Here are the steps to Enable SSH and Crypto Key setup : 2 config must requried for SSH
1 Setup Local VTY line User ID and password
router (Config) # Line VTY 0 15
router (Config-line)# login local
Microsoft Office 2016 Product key Generator 100% Working Activation. Microsoft office 2016 product key generator is a free tool that is used to generate the activation keys for Microsoft office 2016 and make your Microsoft application activated for the lifetime. Though you need to be activation after installation process of Microsoft Office 2016. Microsoft Office 2019 Product Key Generator is a modern tool. Released nowadays with a lot of advance option. Setup is the free week ago to maintain the official authority and has a lot of new things included in it. In Microsoft Office 2019 has added so much addition that was support 32 and 64 Bit. Microsoft office visio professional. May 24, 2019 Microsoft Office Professional plus 2016 Product Key Generator 64bit Free Download. Microsoft Office Professional plus 2016 Product Key is one of the main word processors on the planet. In any case, most normal clients can’t bear the cost of the product. Fortunately, you can locate a free certified Microsoft Office 2016 item key on the web. Apr 04, 2020 Microsoft Office 2019 Professional Plus Product Key. How to Activate Office 2019? First of all, download Office Professional Plus 2019 from here. You can Download Microsoft Office 2019 Crack; Then install Office Professional Plus 2019. Jan 03, 2020 Microsoft Office Professional Plus 2019 License Key Enjoy a fully installed Office experience across PCs, Macs, Windows tablets, iPad®, and Android™ tablets, and most mobile devices. Each user can install Office on 5 PCs or Macs, 5 tablets (Windows, iPad, and Android), and 5 phones.
router (Config-line)# Exit
!!! create local login ID/Pass
router (Config)# username [loginid] password [cisco]
router (Config)# username loginid1 password cisco1
2. router (Config)# ip domain-name example.com
router (Config)# crypto key generate rsa
how many bits in the modulus [512] :1024
router (Config)# ip ssh version2
router (Config)# CTRL Z
Note | Secure Shell (SSH) may generate an additional RSA key pair if you generate a key pair on a router having no RSA keys. The additional key pair is used only by SSH and will have a name such as {router_FQDN }.server. For example, if a router name is “router1.cisco.com,” the key name is “router1.cisco.com.server.” |
This command is not saved in the router configuration; however, the RSA keys generated by this command are saved in the private configuration in NVRAM (which is never displayed to the user or backed up to another device) the next time the configuration is written to NVRAM.
Modulus Length
When you generate RSA keys, you will be prompted to enter a modulus length. The longer the modulus, the stronger the security. However, a longer modules take longer to generate (see the table below for sample times) and takes longer to use.
The size of Key Modulus range from 360 to 2048. Choosing modulus greater than 512 will take longer time.
| Router | 360 bits | 512 bits | 1024 bits | 2048 bits (maximum) |
|---|---|---|---|---|
| Cisco 2500 | 11 seconds | 20 seconds | 4 minutes, 38 seconds | More than 1 hour |
| Cisco 4700 | Less than 1 second | 1 second | 4 seconds | 50 seconds |
Cisco IOS software does not support a modulus greater than 4096 bits. A length of less than 512 bits is normally not recommended. In certain situations, the shorter modulus may not function properly with IKE, so we recommend using a minimum modulus of 2048 bits.
Syntax Description : Optional Strings to embed with SSH Crypto key
| general-keys | (Optional) Specifies that a general-purpose key pair will be generated, which is the default. | ||
| usage-keys | (Optional) Specifies that two RSA special-usage key pairs, one encryption pair and one signature pair, will be generated. | ||
| signature | (Optional) Specifies that the RSA public key generated will be a signature special usage key. | ||
| encryption | (Optional) Specifies that the RSA public key generated will be an encryption special usage key. | ||
| labelkey-label | (Optional) Specifies the name that is used for an RSA key pair when they are being exported.If a key label is not specified, the fully qualified domain name (FQDN) of the router is used. | ||
| exportable | (Optional) Specifies that the RSA key pair can be exported to another Cisco device, such as a router. | ||
| modulusmodulus-size | (Optional) Specifies the IP size of the key modulus.By default, the modulus of a certification authority (CA) key is 1024 bits. The recommended modulus for a CA key is 2048 bits. The range of a CA key modulus is from 350 to 4096 bits.
| ||
| storagedevicename: | (Optional) Specifies the key storage location. The name of the storage device is followed by a colon (:). | ||
| redundancy | (Optional) Specifies that the key should be synchronized to the standby CA. | ||
| ondevicename: | (Optional) Specifies that the RSA key pair will be created on the specified device, including a Universal Serial Bus (USB) token, local disk, or NVRAM. The name of the device is followed by a colon (:).Keys created on a USB token must be 2048 bits or less. |
Crypto Key Generate Rsa Command
| Command | Description |
|---|---|
| copy | Copies any file from a source to a destination, use the copy command in privileged EXEC mode. |
| cryptokeystorage | Sets the default storage location for RSA key pairs. |
| debugcryptoengine | Displays debug messages about crypto engines. |
| hostname | Specifies or modifies the hostname for the network server. |
| ipdomain-name | Defines a default domain name to complete unqualified hostnames (names without a dotted-decimal domain name). |
| showcryptokeymypubkeyrsa | Displays the RSA public keys of your router. |
| show crypto pki certificates | Displays information about your PKI certificate, certification authority, and any registration authority certificates. |