How Does Trezor Generate Keys
- How Does Trezor Generate Keys Work
- How Does Trezor Generate Keys Work
- How Does Trezor Generate Keys 2017
- How Does Trezor Generate Keys Free
- How Does Trezor Generate Keys 2017
When you first set up your Trezor, it will generate the seed for you. When you need to restore access to your wallet, use this offline backup. Dec 24, 2018 Trezor is a hardware wallet which gives exceptional security for managing Bitcoin and other cryptocurrencies private keys.It incorporates and deposits personal keys securely and enables users to carry trade without an Internet link. Trezor grants its users with numerous benefits, as it can be utilized as a safe offline storage system. TREZOR provides top-notch security for bitcoin, protecting against both physical and virtual theft. TREZOR is an HD wallet where you control the private keys, so an entire wallet can be backed up with the 24 words generated on setup. Sep 27, 2019 And that’s it! Recovery is just putting the private keys back into the device. Never enter your recovery seed or any shares on your computer when you’re recovering a Trezor Model T. A common phishing attempt online is when someone spoofs the Trezor website and asks you to.
Puppet generate ssh host keys. I look for a solution to create the ssh host keys for my puppet clients on the puppetmaster. I did some research and found http://jsosic.wordpress.com/2012/12/04. Dec 04, 2012 Generate function calls shell script, and if it’s exit status is 0, ssh::server class includes ssh::server::key class. The latter class defines the ssh host keys (as file resources), sets the correct permissions and reloads ssh service if any of the files/keys changes. Install an SSH module that uses Puppet resources to collect and distribute the public key for each agent node in your Puppet Enterprise deployment. This enables you to SSH to and from any node without authentication warnings. Installs and manages ssh host keys. By default, this type will install keys into /etc/ssh/sshknownhosts. To manage ssh keys in a different knownhosts file, such as a user’s personal knownhosts, pass its path to the target parameter. See the sshauthorizedkey type to manage authorized keys.
Trezor is a hardware wallet providing advanced security for handling Bitcoin and other cryptocurrencies private keys.
Unlike traditional cold storage methods (offline storage or paper wallets), Trezor makes secure payments without exposing your private keys to a potentially compromised computer. See Security philosophy for more info.
- 3Using Trezor
Trezor One vs. Trezor Model T
Trezor One offers everything needed to protect cryptocurrency funds together with advanced features like Password manager or U2F two-factor authorization.
For more information, see Trezor One.
Trezor Model T is the premium version of the hardware wallet. In addition to the functionalities of Trezor One, it has a colored touchscreen for secure on-device input, modern design, an SD card slot, and some other more advanced features.
For more information see Trezor Model T.
See also this comparison table.
How does it work?
Trezor is a small single-purpose computer. It is designed to protect your private keys from possible online and offline risks. To do this, Trezor keeps the private keys away from the Internet and confirms the transactions in-device. That way, you can always check the screen for the right address, amount and transaction fee before sending your bitcoins.
In layman's terms, you can connect Trezor to an infected computer and still be able to have 100% control over the funds in your device.
Find out how exactly Trezor is designed to provide excellent security:
Do you want to know how Trezor protects you against various attack types and what to do in dangerous situations?
How Does Trezor Generate Keys Work
Using Trezor
Trezor Wallet is an easy-to-use browser interface for Trezor. Using the Wallet, you can easily set up the device, manage your cryptocurrency assets, initiate transfers to other services or friends, and more. It is also possible to use your Trezor device with other wallets, eg., Electrum.
Sending transactions
Have a look at how easy and comfortable it is to send transactions:
Receiving address phishing protection
How Does Trezor Generate Keys Work

Make sure that an infected computer has not changed the receiving address you have provided to someone else. The 'Show on Trezor' feature has been developed specifically for this purpose:
Sign & Verify messages
It is also possible to sign and verify messages using Trezor:
Backup and recovery
When first activating the device, you are asked to write down the recovery seed phrase.
This means that in case your Trezor is lost or stolen you can easily retrieve your funds another Trezor or any other compatible wallet.
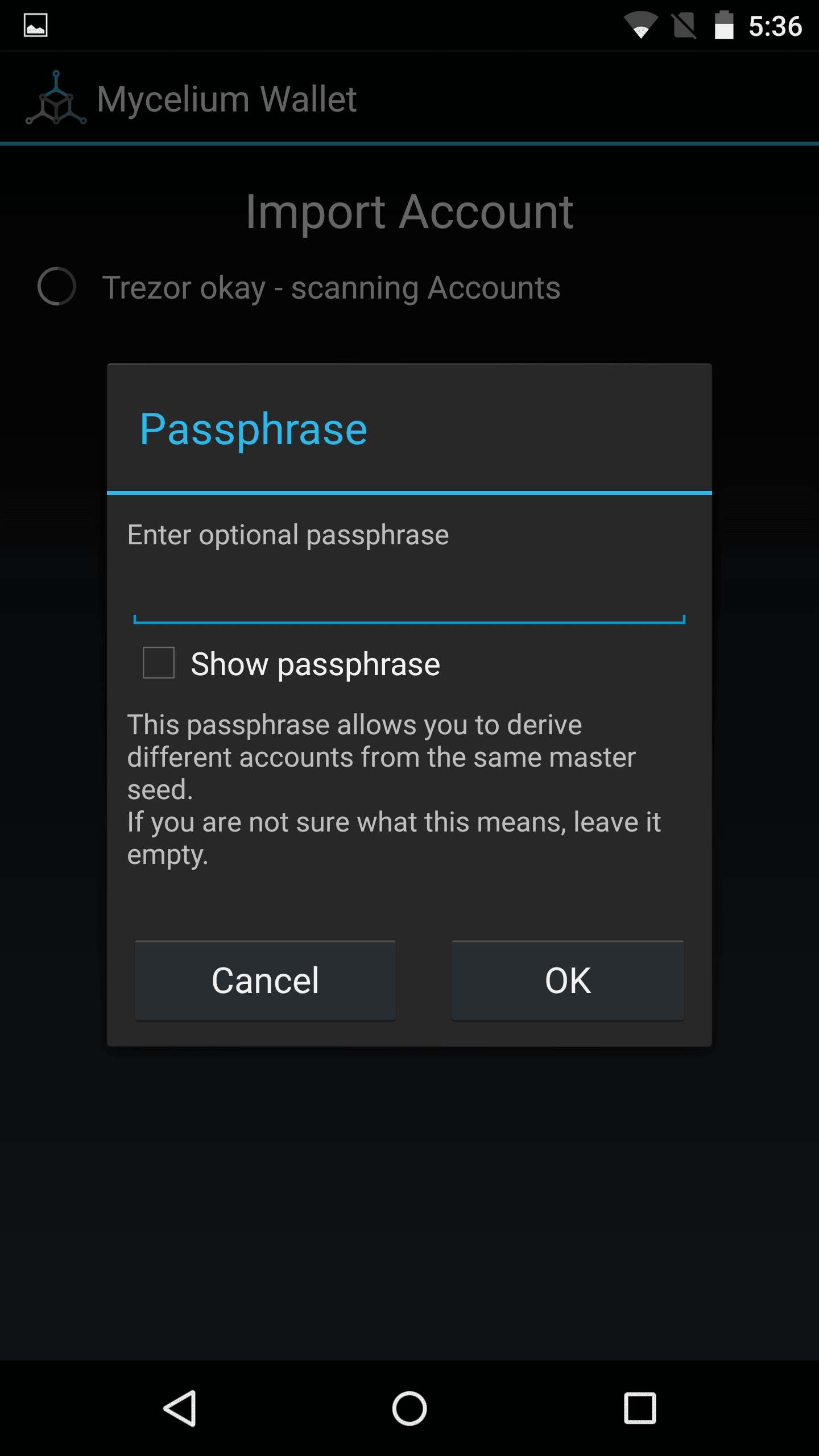
Advanced Settings - Passphrase
You can further improve the security by using a passphrase and or multiple passphrases to create so-called 'Hidden Wallets'. More details here:
Advanced features
How Does Trezor Generate Keys 2017
- U2F
You can use Trezor as your second-factor authentication (U2F) token with services such as Google, GitHub or Dropbox. A further advantage of Trezor is that its users can truly verify what they are about to authorize on the device display.
- Password Manager
The Trezor Password Manager allows users to manage all their passwords and digital identity with the Trezor security and encryption. The Trezor Password Manager does not require remembering one master password, as access is granted by pressing a physical button on your Trezor device. Your passwords are stored on Dropbox or Google Drive in an encrypted form using the private keys derived and safely stored in your Trezor.
- SSH login
With the Trezor SSH Agent, administrators can enjoy passwordless and secure authentication to their servers.