Is A Private Key Required For Sha256 Hash Generator
Brainwallets are Bitcoin wallets generated uniquely from a passphrase that the users keeps in his mind so that it is required and sufficient to move the funds.
But what is actually the process that takes a password and spits a Bitcoin wallet address? Let’s dissect it.
1. From a password to a secret value
So, we have a password, but we need a fixed-size (256-bit) secret value to make our private key. This step can be done in a number of ways as it boils down to hashing the password but is crucial to the strength of the resulting brainwallet.
I need to calculate a SHA-256 hash of a string with a secret key. I found this code: public String computeHash(String input) throws NoSuchAlgorithmException, UnsupportedEncodingException Stack Overflow. Generate a SHA-256 hash with this free online encryption tool. To create a SHA-256 checksum of your file, use the upload feature. To further enhance the security of you encrypted hash you can use a shared key. SHA256 is a part of the SHA-2 (Secure Hash Algorithm 2) family of one-way cryptographic functions, developed in 2001 by the United States National Security Agency (NSA). Hashing functions are cryptographic devices that take as input any string of characters or a file of any type, and then output a computed collision-resistant hash.
Let’s have a look at how popular Brainwallet generators do it. (As of 20131204)
| Generator | Algorithm | Notes |
|---|---|---|
| brainwallet.org | SHA256(password) | |
| bitaddress.org | SHA256(password) | |
| eharning.us/brainwallet-ltc | SHA256(password) | Litecoin wallet |
| brainwallet.ltcbbs.com | SHA256(password) | Litecoin wallet |
| keybase.io/warp | scrypt(password, salt) XOR PBKDF2(password, salt) |
A lot of them just take the unsalted SHA256 hash of the password. This is wrong. Because SHA256 is fast and that means that an attacker can pregenerate huge tables of all possible brainwallets to monitor and empty them (Spoiler: they do). This kind of thing – turning a human supplied password into a public hash – is exactly what password stretching are for, and not using them here is an oversight as bad as not using them to store website user passwords, if not worse since here the hashes (the addresses) are public by default.
(Hint: use WarpWallet. It’s built by people who know what they are doing, and employs a proper KDF, making attacking your wallet really difficult.)

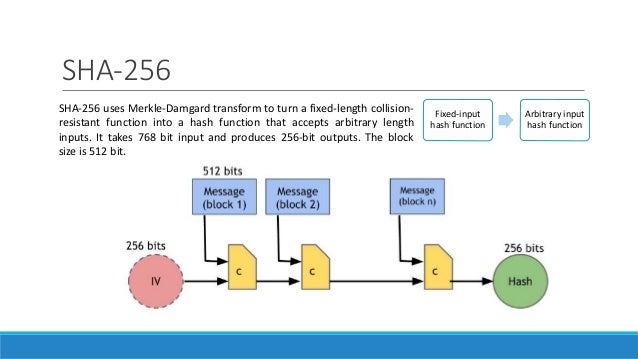
2. From the secret value to a private key
This is step is trivial. Actually, the output of the hashing above taken as a 256-bit unsigned number is already the private key, what is commonly called the secret exponent.
But we are used to see those pretty private keys beginning with a 5, so let’s see how it is encoded. That format is called WIF, Wallet import format, and it is pretty handy as it has checksumming built in and employs a charset without confusing characters (Base58Check) – exactly like a Bitcoin address.
A snippet is worth a thousand words:
3. From a private key to a public key
As Wikipedia tells us a ECDSA private key is just the scalar product of a private key (the secret exponent) and the curve – secp256k1 for Bitcoin – base point. How to do that is complex, but let’s just take it for granted, as you’ll either use a librarty for this or research further by yourself.
What we get out of that operation is a pair (x, y) denoting a point on the curve, our public key.
4. From the public key to a Bitcoin address
We’re almost there! Now we just need to turn that ECDSA public key into a standard Bitcoin address.
The process is the same as point 4, executed on the SHA256+RIPEMD160 hash of the packed x and y values. Dota custom keys generator download. Go go snippet:
And it’s done!
I'm wondering if there is a better solution to my problem?
To ensure my Private Key, CSR and X509 certificate sets match, I'm generating a sha256 hash of the associated public key in der format. The generated values are good and match, hence my confidence that a ECDSA private key, CSR and x509 certificate belong together is good.
However, the onscreen rendering looks something like:
'140095872128928:error:0D07207B:asn1 encoding routines:ASN1_get_object:header too long:asn1_lib.c:150:'
The three forms of command line queries I use are:
Create sha256 hash from ECDSA p256 Private key
openssl ec -in alice-ECDSA.key -inform PEM -pubout openssl asn1parse -strparse 23 -out alice-ECDSA-key-pubkey.der
sha256_value=openssl sha256 -c alice-ECDSA-key-pubkey.der
Create sha256 hash from a CSR p256 public key
openssl req -in alice-ECDSA.csr -inform PEM -pubkey -noout openssl asn1parse -strparse 23 -out alice-ECDSA-csr-pubkey.der
sha256_value=openssl sha256 -c alice-ECDSA-csr-pubkey.der
Create sha256 from Public Key Certificate p256 public key
openssl x509 -noout -in alice-ECDSA.pem -pubkey openssl asn1parse -strparse 23 -out alice-ECDSA-x509-pubkey.der
sha256_value=openssl sha256 -c alice-ECDSA-x509-pubkey.der
I'm wondering is this an issue? or simply a result of my approach to generating the SHA256 hash of the der encode public key?
Is A Private Key Required For Sha256 Hash Generator Manual
Regards
Nigel